TIBER: Threat Intelligence-based Ethical Red Teaming
Knowing One’s Demands – Implementing the Framework
In 2018, the member institutions of the European System of Central Banks (ESCB) agreed upon a framework for threat-led penetration tests – TIBER-EU. This framework is implemented by the EU member states individually: in Germany, for example, as TIBER-DE.
It differs from our conventional red teaming assessment as follows:
- The respective central bank oversees the test with a TIBER cyber team (TCT).
- In advance, a threat intelligence (TI) phase is carried out to analyze the threat situation.
- Various scenarios with intrusion vectors and target systems are defined.
- The red team creates a test plan for actioning the scenarios.
- A replay workshop and purple teaming are required.
- Based on the red team report, the blue team creates a report with the countermeasures taken.
- The white team creates a remedial action plan.

You are interested in TIBER tests?
Steffen Stepper
steffen.stepper(at)syss.de
redteam(at)syss.de
+49 (0)7071 - 40 78 56-6157
PGP Key
We will gladly support you with continuous project consulting in all phases from "We are thinking about conducting a TIBER test." to "The test is over, what now?"
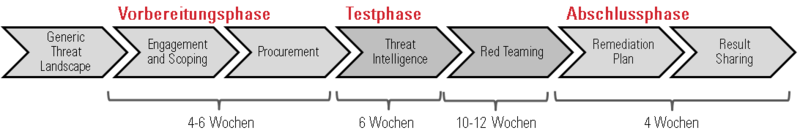
1. Preparation Phase
Part of the preparation phase are initiation, kickoff and scoping.
Initiation:
A TIBER test manager from the central bank presents the country-specific test process, e.g. TIBER-DE, to the white team and informs the team members of their roles and responsibilities.
Kickoff:
In the kick-off workshop, both the red team provider and the threat intelligence provider are introduced to the test and informed about what happens next.
Scoping:
In the scoping step, the critical functions of the company are analyzed. A suitable basis for this is a current business impact analysis in combination with a protection requirements assessment. If a very high protection requirement is identified particularly in the domain of integrity, confidentiality or availability, this should be defined in the scope. When the scope is being defined, a great number of targets (flags) could emerge and these should be prioritized afterwards. With the conclusion of the scoping step, two documents are available: the project plan and the scope specifications.
2. Test Phase
Threat intelligence:
The current threat situation of the financial company is analyzed. For this purpose, the central bank contributes the report on the threat situation at national level. Current attack vectors are also collected specifically for the company under test and a profile is created. In addition, possible threat scenarios are determined for the respective flags (targets) that were developed previously as part of scoping.
Red teaming:
In consultation with the threat intelligence team, the red team develops possible attack paths for the respective flags. A test plan is created, which is discussed and agreed with the white team. When approval is granted, the test starts. Due to the creative approach in which the test is undertaken, variations from the plan could arise.
With the conclusion of the test phase, two documents are available: a report on the threat situation of the company, and the test plan.
3. Completion Phase
The completion phase involves the steps "creation of test reports", "replay and feedback", "remedial action plan and final report" and "certification and passing on of results".
Creation of test reports:
The red team creates a test report containing a timeline of the attacks performed. Based on the timeline, the blue team creates its own test reports with the countermeasures taken and discoveries made.
Replay and feedback:
The attacks are presented by the red team and discussed with the blue team. It is expressly desired here to play through the possible problem-solving strategies for successful attacks in the purple team approach.
Remedial action plan and final report:
The tested company then creates a remedial action plan, which is part of a final report. This final report intentionally contains no technical details, which is important because the report is given to the central bank where it is not supposed to become part of a collection of "hacking instructions".
Certification and passing on of results:
The TIBER cyber team of the central bank gives further advice as part of an evaluation workshop and receives the final report containing the remedial action plan.
At the end of the completion phase, four documents are available: the test reports of the red team and blue team, a remedial action plan and a final report.
DO NOT HESITATE TO GET IN TOUCH +49 (0)7071 - 40 78 56-0 or anfrage@syss.de | OUTSIDE REGULAR OFFICE Hours CALL +49 (0)7071 - 40 78 56-99
As a framework contract customer please dial the provided on-call service number
DO NOT HESITATE TO GET IN TOUCH +49 (0)7071 - 40 78 56-0 or anfrage@syss.de
OUTSIDE REGULAR OFFICE Hours CALL +49 (0)7071 - 40 78 56-99
As a framework contract customer please dial the provided on-call service number
GET IN TOUCH
+49 (0)7071 - 40 78 56-0 or anfrage@syss.de
OUTSIDE REGULAR OFFICE Hours
+49 (0)7071 - 40 78 56-99
As a framework contract customer please dial the provided on-call service number